Welcome to our SECURITY blog! This is a topic that I could talk about for hours, but don’t worry, I won’t go too technical – I’ll keep things as simple as I can, but it could get a little nerdy.
I’m sure we all remember the days when a password with plenty of unusual characters was enough to keep you safe online, there were less phishing attacks, fewer ransomware attacks, less email spoofing and less spam in general! But as technology has advanced, so has cyber attacks.

Let’s start by identifying some of the primary attacks that we see on clients systems:
A Phishing attack is when someone sends you an email asking for you to authenticate your login details. A classic phishing attempt or attack may be a Telstra looking email, but if you look at the email address, it is actually somebody else trying to get to your Bigpond email address.
Email spoofing is a tricky one to explain, the most simple explanation I can provide is that it is somebody trying to send email as if they were coming from your email address. They are essentially copying your email address and using it to send an email out in the hope that they can trick someone into paying them money or gaining access to their systems
Ransomware is a particularly nasty type of malware that is ultra disruptive, it works by attaching a link that you click on from an email or an attachment from an email, or it could simply be something that you click online that loads a small program in the background of your computer which then starts a process of encrypting all of your personal data. It then displays a message to allegedly get your money back by paying ransom money to an undisclosed entity or person. In every case, we have ever seen if you pay the money your data still stays encrypted, and you ultimately lose your money.
Spyware collects information about users’ activities without their knowledge or consent. This can include passwords, pins, payment information and unstructured messages. The use of spyware is not limited to the desktop browser; it can also operate in a critical app or on a mobile phone.
Adware tracks a user’s surfing activity to determine which ads to serve them. Although adware is similar to spyware, it does not install any software on a user’s computer, nor does it capture keystrokes.
The danger of adware is the erosion of a user’s privacy. The data captured by adware is collated, overtly or covertly, about the user’s activity elsewhere on the internet and then used to create a profile of that person including who their friends are, what they’ve purchased, where they’ve travelled, plus more. That information can be shared or sold to advertisers without the user’s consent.
A Trojan disguises itself as desirable code or software. Once downloaded by unsuspecting users, the Trojan can take control of victims’ systems for malicious purposes. Trojans may hide in games, apps, or even software patches, or they may be embedded in attachments included in phishing emails.
Worms target vulnerabilities in operating systems to install themselves into networks. They may gain access in several ways: through backdoors built into the software, through unintentional software vulnerabilities, or flash drives. Once in place, worms can be used by malicious actors to launch DDoS (distributed denial-of-service) attacks, steal sensitive data, or conduct ransomware attacks.
A rootkit is a software that gives malicious actors remote control of a victim’s computer with full administrative privileges. Rootkits can be injected into applications, kernels, hypervisors, or firmware. They spread through phishing, malicious attachments, malicious downloads, and compromised shared drives. Rootkits can also be used to conceal other malware, such as keyloggers.
A keylogger is a type of spyware that monitors user activity. Keyloggers have legitimate uses; businesses can use them to monitor employee activity, and families may use them to keep track of children’s online behaviours.
However, when installed for malicious purposes, keyloggers can be used to steal password data, banking information and other sensitive information. Keyloggers can be inserted into a system through phishing, social engineering or malicious downloads.
Secure & protect your data
The single biggest question we’re asked is “how secure is your security system?”
To keep things simple, we use a multi-layered security strategy. Between onsite firewalls, comprehensive Microsoft security policies applied to your organisation and an upgraded antivirus we have the tools to keep you safe online – all of which operate whether you are in your office of working from home
We have recently completed testing on a new form of antivirus known as EDR (Endpoint Detection & Response). This system is driven in real time by artificial intelligence which helps detect, prevent, and respond to changing threats.
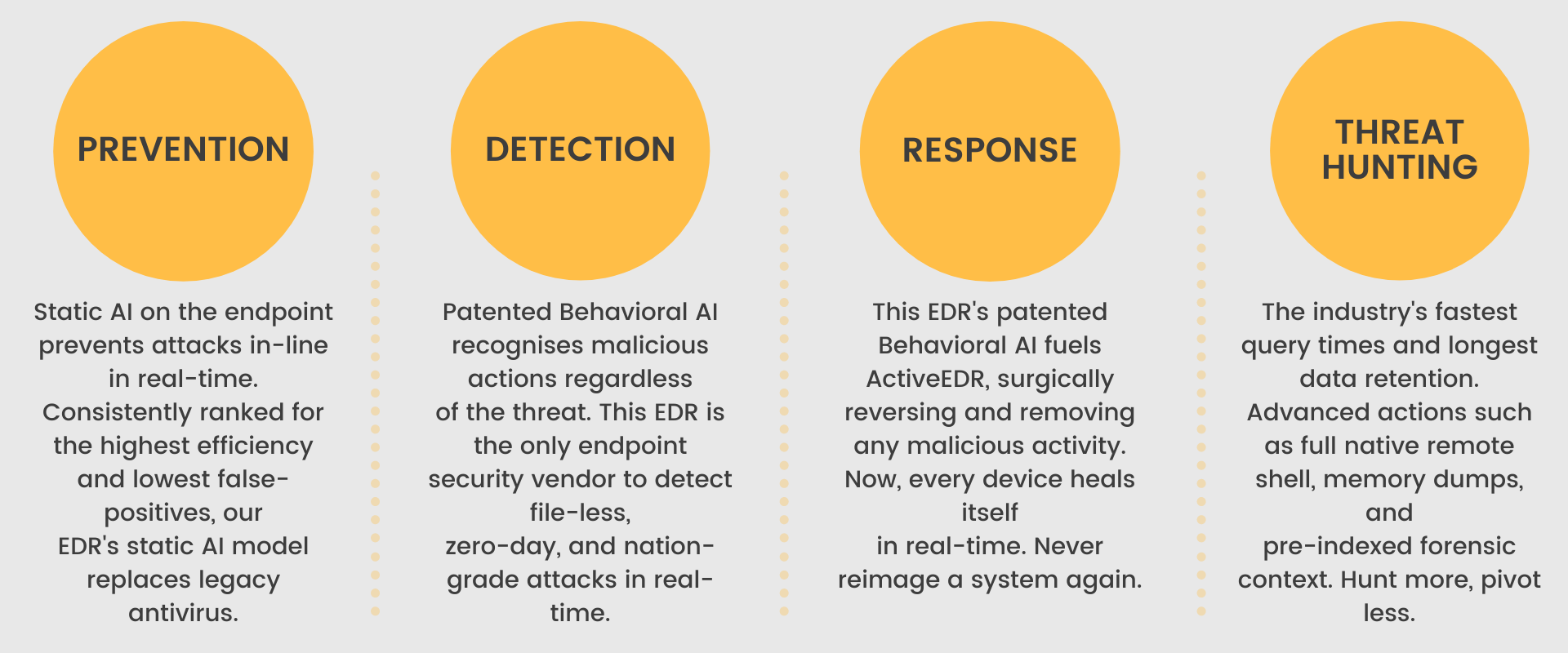
We create multiple security policies via the Microsoft secure platform and apply them organisation-wide to enable full data tracking, end-user data access history and granular data access for disruption-free computing.
It is at this point I realise I could keep talking forever about security! The key takeaway from this blog is cybersecurity needs to be viewed as a multi-layered system that starts with the end-user and simple multifactor authentication.
Thanks for reading today – post your comment below and don’t forget to subscribe to our newsletter here.